
It’s a misty five o’clock in the morning, and suddenly a few key servers on your network go down. You’re busy sleeping, so you don’t find out about it until your users get in and raise a fuss. By the time you arrive, your boss is frothing at the mouth and you’re looking for somewhere to hide. Welcome to the world of being an IT manager. And, no, this hasn’t gotten easier now that we’re all working from home due to the pandemic. If anything, it’s become more difficult, since you’ll need to find out about problems and solve them, during a time when it’s not so simple to set foot inside your data closet. Fortunately, the tools to make that process easier are numerous and mature. They’re general purpose network monitoring tools, and we’ve tested and ranked the top players.
What Is a Network Monitoring Tool?
There are two major categories of monitoring tool. The first is what’s called an agentless platform. This is typically installed on premises, meaning on a server or workstation that’s physically attached to your network. This analyzer will also need all the access credentials for each of the systems and services that you want to monitor. This approach has advantages in that it doesn’t need to be installed on each individual device, and it can automatically discover and categorize the devices on your network with minimal effort on your part. The drawback is that you typically need a dedicated system with enough horsepower to run the software and its supporting database; and if you have more than one office, you’ll probably need such a muscled machine in every one of them.
The other method is an agent-based system. These tend to deliver a large part of the solution in a software-as-a-service (SaaS) model, which just means you’ll be accessing the software via the web (though this may bring security considerations to the fore depending on the business). Agents, or monitoring programs that live on each individual device, will run and report back on important telemetry. The advantage of this method is that you can typically get more in-depth data than using an agentless system, since the agents will generally have a greater level of hardware access. The disadvantage is that the agent application will need to be installed on each individual device you’re monitoring and that can get sticky even with automation. For one thing, it can cause problems if devices don’t support the operating systems that the agent software wants for installation.
A third type of tool, which we didn’t include in this roundup, is the specialist category. Generally, these include security monitors and scanners as well as wireless network analyzers, like Ekahau Pro. Taking that product as an example, while it has some overlapping features with the tools we’ve reviewed here, like traffic analysis, it’s also lacking some, such as a web-based interface or remote control. That’s because Ekahau is a specialist; it’s purpose-built for a very specific mission, namely wireless network configuration at scale. That means it has several capabilities you won’t find in the tools we’ve reviewed as part of this roundup because they simply don’t need them.
One example is CAD-generated floorplans that map out your wireless signal strength because they come with numerical values that factor in the density of walls, doors, and windows and how these affect your wireless throughput. Ekahau uses this data in a proprietary mapping and hotspot application to not only monitor your wireless network, but also generate what-if scenarios for different office construction materials versus access point placement. That’s fantastic for wireless network specialists, but you couldn’t use Ekahau to replace an all-up network monitor when it comes to things like remote device health for wired infrastructure.
So bottom line, a specialist tool may sound like it can handle general network management, but they usually can’t cover as many device and service types or even management features as the tools we’ve reviewed here. They will offer handy features you can’t find in these tools, however, so just make sure you need those and be careful when adding one to your IT tool set.
(Editors’ Note: Ekahau is owned by J2 Global, the parent company of Ziff Davis, the publisher of PCMag.com.)
How We Test Network Analyzers
Whether you’re using an agent-based or agentless system, there are several aspects that we look at when scoring these solutions. One of the most important components is ease of use. No matter how sophisticated a piece of software might be, if the learning curve is cripplingly high then that’s time lost where your devices aren’t being monitored and your IT staff is doing something other than managing infrastructure. In many cases, support and documentation play a significant role, but there are also cases where the interface is clearly lagging behind other systems in the same class. You want a tool that an IT manager familiar with networking technology can understand quickly, so you can get it working on your network as soon as possible.
Another very important hands-on capability, certainly at the early stages of deployment, is how the software adds devices. After all, these are essentially tools for monitoring a large number of different endpoints and how they’re working together. Even a small to midsized business (SMB) can have not only several dozen switches, routers, and even firewalls at its central office; it can also have several such devices at every branch office, too. To effectively monitor hundreds or even thousands of devices, you need to be able to tell the software exactly which devices you want it to track, where they are, and what it is you want to know about them.
You can do this on a device-by-device basis, or via something called auto-discover. This simply refers to a monitoring system’s ability to scan a network and report back with a list of all the devices it finds. Administrators then simply modify those devices that need it and then the software automatically adds them to its list of monitored targets. While this tends to be a less important issue in agent-based systems, since you’re going to have to install software on each monitoring target anyway; for agentless systems, it needs to be as painless as possible because it’s a big part of the overall installation process. The best systems will default to the most commonly used options, but make advanced features available for those users that need them.
After this, we consider how easy it is to add individual devices manually. Typically, no auto-discovery process finds everything, so you need the ability to force the system to look at a particular device it missed during its scan. This should include the ability to add services as well as just endpoint devices, like wired and wireless routers, switches, and firewalls. These tend to be a bit more complicated to monitor, but they’re among the most important devices when it comes to the overall health of any network. That’s why, during testing, we treated this as a major consideration.
Don’t Forget Software Defined Networks
Also very important these days, especially now that so many networks are being managed remotely, is the ability to support virtualized infrastructure and software-defined network (SDN) environments. This can include everything from the virtual servers you many have installed in an infrastructure-as-a-service (IaaS) public cloud to even the smallest virtual containers you’re using to serve up individual applications.
Even most SMBs today run much of their on-premises servers mainly as virtual machines (VMs) living on a large hypervisor ecosystem. That’s because the benefits of VMs over physical servers are simply too many to ignore, not only for IT managers, but for CEOs and CFOs, too. These include lower costs, increased return on investment (ROI), and much more flexible management. However there are potential downsides, too, or at least issues you’ll need to address before choosing a primary network monitor to handle virtualized endpoints.
Mainly, it’s that these hypervisor environments, notably VMware’s ESXi and Microsoft’s Hyper-V, have their own set of standards that need to be supported by any analysis tool that’s looking to get management data out of them. Vendors need to specifically support the ability to detect and monitor hypervisor environments and their virtual machines, many of which bring their own challenges. For example, VMware ESXi has a free tier called ESXi that doesn’t include the company’s vSphere management environment. Being able to support ESXi without this is a huge bonus, unless you’re using both it and vSphere anyway.
That’s why, aside from testing all the general monitoring components, we also look at each of these tools as a whole. What is each tool’s optimal monitoring environment and how easy is each system to setup and use? Generally, defining monitoring targets hinges on some form of template being available for different kinds of device types and service applications. Some options might include things like HTTP (Hypertext Transfer Protocol), SSH (Secure Shell), SFTP Secure FTP), or SNMP (Simple Network Monitoring Protocol). Administrators fill out these templates with the appropriate device or service information, name them for the service in question, and then add them to the monitor’s database. The fewer clicks we make and fields we need to fill out, the better as far as our testing results. If advanced options are available but don’t come into play as hurdles, this also adds to the final score.
Naturally, aside from monitoring individual devices and systems, informing administrators of problems is critical, too. So we put a high degree of value on how each system goes about setting up alerts. Knowing immediately when there is a severe problem can often mean the difference between getting a problem resolved quickly and causing a disaster on the business’ front lines. While email is the primary way most of these notifications work, today’s plethora of online collaboration technologies can give you many more options, and all these tools should support at least some of them.
For our testing, that means looking for things like the ability to launch third-party response applications, initiate SMS messages, and kick-off other online services, like IFTTT (If This Then That). The more flexible the overall alerting process is the better we rank it because it gives customers more workflow options. However, that flexibility needs to be balanced by ease of use.
Reporting is our final criteria, but it’s a critical component to any network monitoring app. These tools collect data that IT managers need to use immediately in order to keep networks up and running. So how the tool presents this data is a key factor to success. Also, while that immediate data is certainly important, IT administrators also need longer term metrics to see how changes affect overall performance over time.
Other Important Features for Network Analysis
All of the above are important capabilities in a general-purpose network monitor, but there are other key features, too, even if they might not apply to every network. For one, from an administrator’s perspective, it’s nice to have visual graphics that give you a quick overview of not only the network’s current status but visual drill-down to individual device health, too. This isn’t the same as reporting and several of the tools we tested clearly stood out in this regard. Having the ability to tweak the arrangement of graphical elements on a dashboard is an added plus.
IP Address Management (IPAM) has become a vital capability for many large organizations, and having the ability to monitor this is important. Keeping track of statically assigned addresses, along with a large number of DHCP pools, can’t be adequately managed with a manual system. Integrating IPAM with a network management tool just makes sense as the same person frequently handles both functions.
Automation is also key to managing large numbers of devices. The more you can automate small administration tasks, the more efficient the process becomes. This is a difficult feature to quantify since vendors tend to approach it differently, but automated alerting and repair fall into this category and represent a key differentiator between products.
Lastly, and a critical feature now that so many employees (which means endpoints to an IT professional) are located at home, is remote access. You need to be able to remotely access both the network monitoring tool as well as the endpoints and networks it’s managing.
How to Buy the Right Network Scanner
The first step for any IT project is to define the requirements. We’ve listed numerous important capabilities above. But you can break these down into categories and also look for key basic capabilities before even considering the more advanced ones. For example, you need to see detailed information about key pieces of your network hardware, such as switches and routers. So how difficult is this to access and exactly what information will you get?
Many organizations don’t have the staff to monitor computer screens 24/7. That makes automated alerting, escalation, and remediation all very important requirements for most companies. But don’t just look to see if those features exist, carefully evaluate how they work and make sure it’s what your IT staff needs. Trend-based reporting and monitoring help determine utilization levels and identify potential bottlenecks before they become a problem. Good reporting tools are another requirement, but for many companies that also means the ability to create customized reports and queries.
Once you have that list of essential requirements, you should be able to look at each one of these products and determine if they qualify. If more than one product qualifies, you’ll need to do some testing on your own to see which one best suits your needs. That’s where a free evaluation version is important, and you’re looking to access it for 30 days at least.
Finally, there’s pricing, though for most network managers this isn’t a paramount criteria for the overall purchasing decision. Match your needs to the tool, then worry about pricing. That’s a good approach because pricing is varied in this segment, likely because so many contenders still use an on-premises deployment model, which necessitates old-fashioned, on-premises licensing.
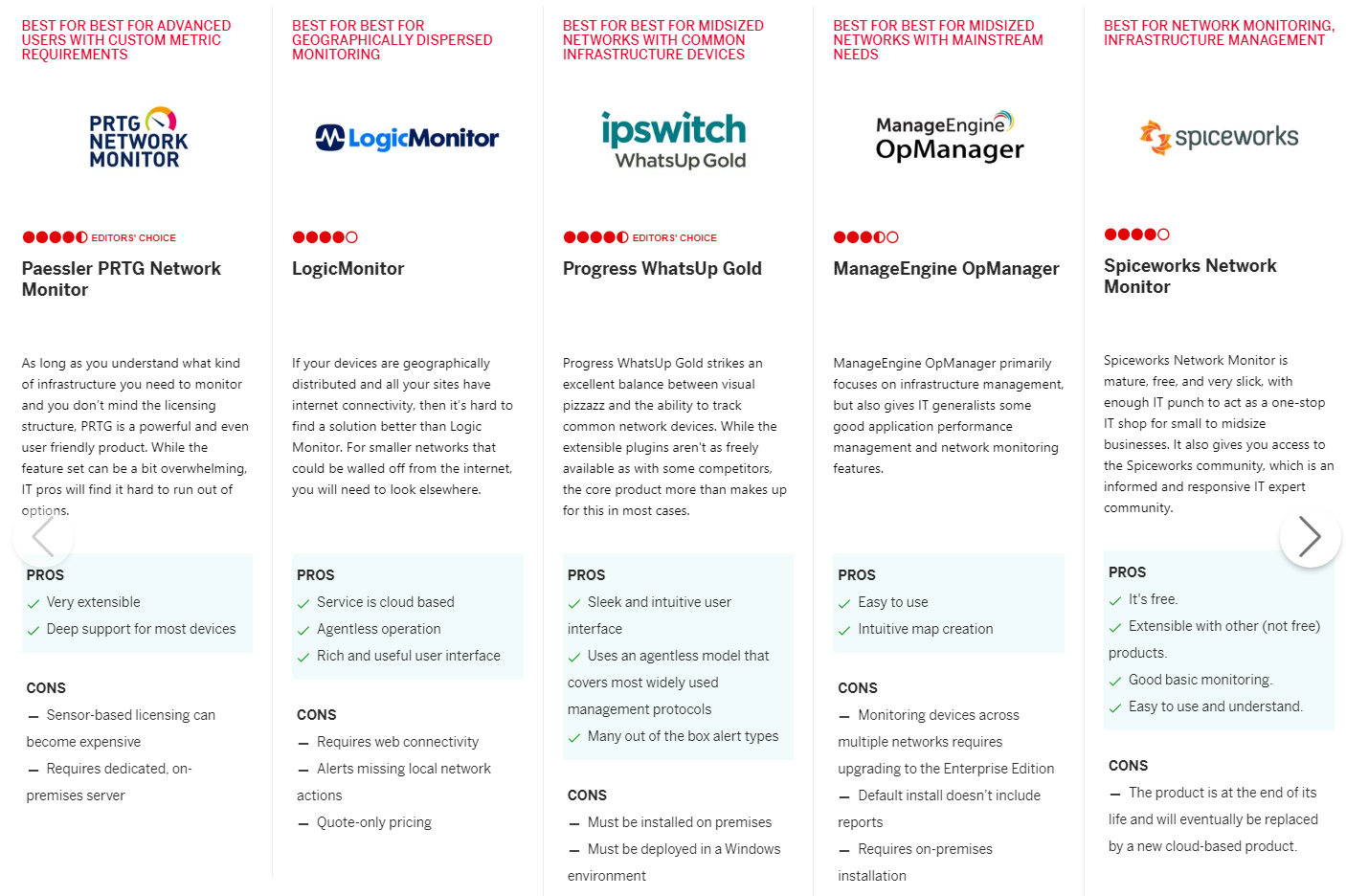
Chi tiết so sánh tại: https://sea.pcmag.com/cloud-services/8061/the-best-network-monitoring-software-for-2020#roundup-table
more recommended stories
 Enscape bản quyền – Phần mềm render kiến trúc theo thời gian thực
Enscape bản quyền – Phần mềm render kiến trúc theo thời gian thựcTệp khách hàng đến 85% đến.
 Công cụ thiết kế ERD diagram trong dbForge Studio for SQL Server
Công cụ thiết kế ERD diagram trong dbForge Studio for SQL ServerIworld.com.vn – Cùng tìm hiểu về.
 Query Builder – Trình tạo truy vấn dữ liệu trong dbForge Studio for SQL Server
Query Builder – Trình tạo truy vấn dữ liệu trong dbForge Studio for SQL ServerIworld.com.vn – Cùng tìm hiểu về.
 Data Import and Export tool trong dbForge Studio for SQL Server
Data Import and Export tool trong dbForge Studio for SQL ServerIworld.com.vn – Cùng tìm hiểu Data.
 7 lý do khiến dbForge Studio for SQL Server trở thành công cụ thiết kế và mô hình hoá database SQL Server
7 lý do khiến dbForge Studio for SQL Server trở thành công cụ thiết kế và mô hình hoá database SQL ServerIworld.com.vn – Cùng tìm hiểu 7.
 Pivot Table trong SQL Server – tích hợp trên dbForge Studio for SQL Server
Pivot Table trong SQL Server – tích hợp trên dbForge Studio for SQL ServerIworld.com.vn – Cùng tìm hiểu về.
 Top 10 phần mềm PDF hàng đầu hiện nay
Top 10 phần mềm PDF hàng đầu hiện nayIworld.com.vn xin gửi tới độc giả.
 Top 21 công cụ Work from Home để giúp bạn làm việc từ xa dễ dàng
Top 21 công cụ Work from Home để giúp bạn làm việc từ xa dễ dàngBài viết đang chờ dịch sang.
